May 1, 2025 Software Development
API Development Best Practices in 2025: A Complete Guide
May 1, 2025 Software Development
Table of Contents
May 1, 2025 Software Development
As we head into 2025, API Development has become crucial. You see, in the current tech era, APIs are the beats that allow different applications and services to jam.
Whether you’re building internal microservices, crafting mobile experiences, or working with external partners, how you design and the quality of your APIs can literally make or break your digital projects.
But here’s the thing: making effective APIs isn’t just about connecting stuff. Nope, it’s about building strong, scalable, secure, and user-friendly pathways that can last. This guide takes a fresh look at API Development, digging deep into the best practices that will really matter in 2025. We’re not just skimming the surface here; we’ll share practical tips and strategies for those who want to create top-notch Application Programming Interfaces.
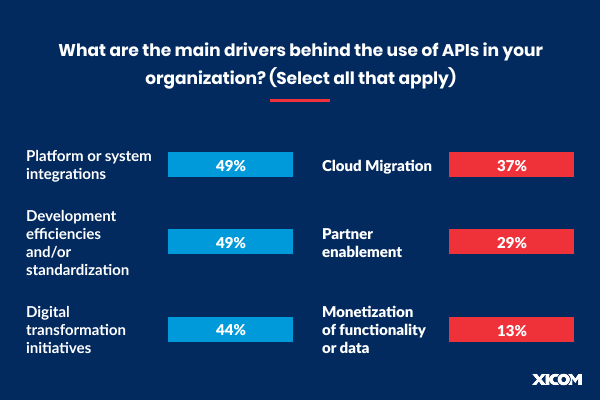
In reality, 48% of organizations leverage APIs for use in platform or system integration.
So, whether you want to hire software developers who know their way around APIs or optimize your existing API Development processes to be current with 2025, this guide has you taken care of with the information and best practices necessary to develop Application Programming Interfaces.
So, let’s start.
Let’s keep it basic. An API (Application Programming Interface) is essentially a collection of rules and procedures that enables various software programs or applications to communicate with one another and exchange information or use one another’s capabilities. It’s kind of a language that various apps can converse in.
Let me clarify:
Today, in 2025, APIs are not technical interfaces anymore; they’re strategic assets. They’re digital transformation engines that help businesses interact with customers, partners, and internal systems in new and creative ways.
Some reasons to have API development are as following:
Now, you might be thinking-
So, we know APIs are like digital waiters, but how exactly do they take our order and bring us what we need? Let’s take a simpler look at the steps involved when apps talk to each other using APIs:
Think of it like ordering food online:
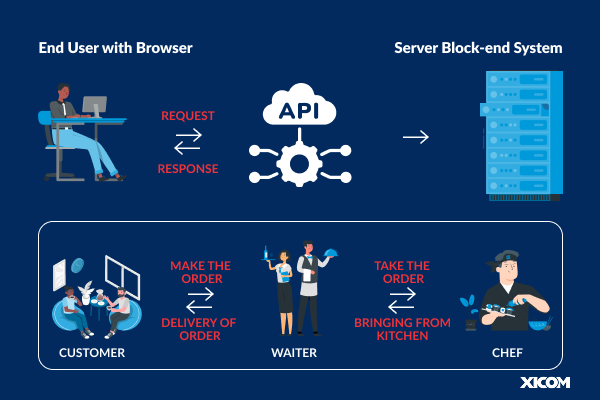
Similarly, when you navigate through a Zomato app or website to order your food, a computer program (the client app) sends a particular message (an API request) to another machine (the server) via a particular gateway (the API gateway).
It’s not simply “I want food!” It’s highly specific, e.g., “I want the Italian restaurant menu” or “Order one Margherita pizza.”
This message adheres to a pre-established set of standards (a protocol, e.g., talking English on the net) and contains all the information that the client application needs in order to converse – perhaps it needs the server to retrieve some information (such as a friend’s photo) or to instruct the server to do something (such as posting an update).
The API gateway is the restaurant front desk. It accepts the client app’s request.
It first verifies whether the request is valid – such as verifying that you are ordering from the correct restaurant and through the correct online ordering system. This may involve verifying a special key (an API key) that will recognize the client app.
For trusted requests (for example, reading confidential data), the API would potentially also need to authenticate that person requesting the request and that they are authorized to do so (this is auth and auth – for instance, you logging into your account and being entitled to view your order history).
After the API has established that the request is authentic and approved, it starts to work. That is like the kitchen starting to prepare your food.
Based on what the client app requested, the API could:
One requests something in a certain manner, the API ensures that the request is orderly, retrieves the data or carries out the action, and returns a well-formatted response which the requesting program can interpret and utilize. It’s all about nice processes and good communication in the background to enable our apps to cooperate well.
Now that you have a better grasp of what API development entails, let’s get familiar with some of their types.
Let us discuss the different categories of APIs you may come across in the world of software development:
There is no singular method through which all APIs could be classified, but some popular classifications based on diverse parameters are as follows:
It groups APIs according to the central technology and methodology used in implementing the API.
This is one of the most popular architectural styles for web APIs. RESTful APIs are:
SOAP is a more conventional and typically more complicated protocol. The most significant features are:
RPC is a more straightforward form of API where the client can call a function or procedure on the remote server as a local function call.
API Development forms the backbone of software design these days, integrating incompatible systems to make them compatible and also distributing useful resources. APIs need to be designed in a secure, scalable, and maintainable manner, and thus strict API Development Best Practices need to be followed.
This helpful guide discusses the majority of important things for anyone who cares about building an api best practices from scratch right up to maintenance.
The technique of how to develop an API effectively is one that includes a methodical approach and a culture of quality every time. Collaborating with a trusted software development firm in India that values these principles can have a huge impact on the success of your API projects.
API Development can be divided into some key steps, each of them are:
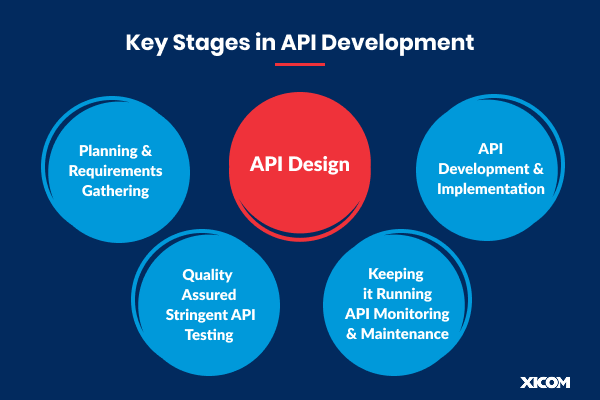
Planning stage is the foundation on which a successful API relies. It is where “why” and “who” are given proper attention before technical ones. Poor planning is a frequent fallacy which may result in APIs that are devoid of user-need orientation, hard to keep up with, or fail in their business purpose for which they have been developed.
This phase is vital in mind when it comes to how to develop an api that works. Remaining consistent with api best practices in this phase will set an API that works and is easy to utilize.
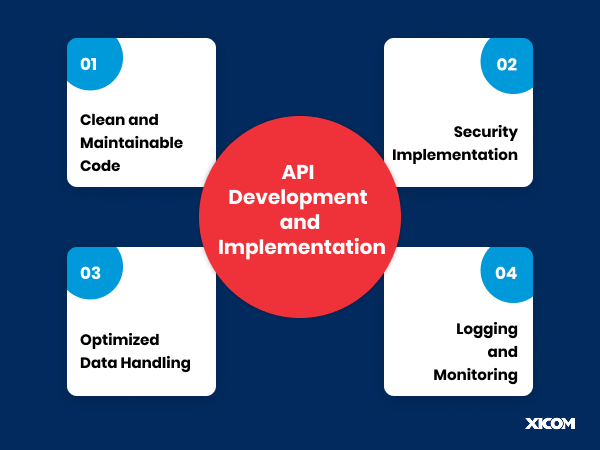
API Development stage is where design comes to life in the form of code. Coding standards, such as security features, and data handling optimization are most important.
Complete testing is not a compromise when it comes to API Development. It makes sure that the API functions as intended, is secure, and is performance-worthy.
Deployment is not the final step in the API Development lifecycle. Continuous monitoring and maintenance are required to keep the API healthy and growing.
Building an API that gets along – an API that is safe, reliable, and a joy to work with by others – requires more than code. It requires good sense principles applied from the beginning. Let’s examine some of the best practices to assist you in building the right API:
Drive a highway on a rush hour afternoon. Without traffic rules or lights, it would soon turn into a nightmare and unusable disaster. App Throttling is similar to putting traffic lights for your API. It is an intelligent way of managing the flow of incoming requests so that your API doesn’t get clogged.
Throttling is similar to a defense mechanism that ensures your API works in a smooth way and protects it from overloading and attacks, and provides the same access to everyone.
When you’re building an API, you typically end up with some form of hub or center of entry known as an API Gateway. Think of your gateway as an intelligent security guard standing at your digital services entrance.
Your API gateway is your front-line security and single point of management for your API, granting only the correct people access to the correct data and enabling you to secure and control your services.
When computer programs talk to APIs on the internet, they send out standard requests like GET (to get something) and POST (to put something). They are literally instructions. Occasionally, however, the path such instructions travel (like some old web frameworks called proxies) might only respond to these basic “GET” and “POST” instructions but not others (like PUT to modify or DELETE to remove).
To circumvent this limitation, we can make use of the mechanism of enabling programs to “override” the intended command. Normally, one does this by including a special directive in the message, for example, saying “Despite my using the ‘POST’ pathway, treat this as being a ‘PUT’ command.” One method of doing this is by using the placement of a special flag in the “header” of the message by the name X-HTTP-Method-Override.
It’s essentially educating the API on a secret code in hopes of getting it to do what you really want it to do, even when the normal avenues of the internet are partially clogged. That makes your API platform-compatible across different systems.
Today we have smart tools that can automatically in real-time monitor your APIs and infrastructure for you. That is superior to having a developer manually do it all the time. These tools can discover potential issues such as:
Tools such as AWS CloudWatch are car diagnostic tools for your digital infrastructure. They keep an eye on your API and the surrounding infrastructure 24/7 and can notify you of potential issues before they lead to significant downtime. This allows you to maintain your API running and operating smoothly and reliably without having someone in front of it 24/7.
For APIs, one security/usability compromise is typically token-based authentication. Here’s the general procedure:
When a user or application first tries to access the API and verifies that they are who they say they are (usually by authenticating once), the API gives them a temporary “token” – like a type of keycard.
For every subsequent request, the user or app needs only provide this token. The API is able to validate the token in a hurry without having to request login credentials for every request.
This makes the API safer (because you’re not continually sending passwords) and more convenient (because you only need to log in once to get the “keycard”). You want good security that has good performance that will not pester good users.
Picture purchasing a brand new piece of furniture with absolutely no instructions to assemble it. It would be very frustrating and take a long time to assemble, if it can even be done. APIs are the same. If you want other coders to have the ability to figure out how to use your API for their mobile apps or whatever they will be doing with it, you must have very good documentation.
A good API documentation is like an incredibly long instruction guide. It needs to be capable of explaining well:
With good API documentation, it is much simpler for other developers to learn about your API and begin using it in a short time. This results in
In short, investing in good and proper API documentation is akin to giving other developers a clear directions guide, so it is infinitely more likely that they will be able to use and profit from your API successfully.
API Development in 2025 requires multidisciplinary practices including sound design practices, cautious architectural design choices, adequate security controls, performance tuning, beautiful versioning, full documentation, solid testing, reasonable monitoring, and compliance with automation and collaboration.
By following these API Development Best Practices, you also need to hire software development company in India to create APIs that are secure, scalable, maintainable, and a delight to use, and ultimately drive innovation and success in the hyper-connected digital world.
Keep in mind that developing an API best practices is a continuous process of learning and improvement. Be inquisitive, adopt new technologies, and always cater to the needs of your API users.
API development is the act of creating sets of rules and regulations based on which sets of software programs may talk to and share data with one another. The procedure of developing API interfaces demands design work along with coding and testing and post-launch maintenance to make different systems integrate their operational features and information.
To develop efficient APIs for mobile apps, designers should implement modification timestamps along with search by criteria for data update efficiency as well as paging for big datasets combined with sorting for ordered data retrieval through JSON support and RESTful design and OAuth authorization for quick, secure access.
GitHub operates as a well-known open-source platform for git repository hosting where developers keep control of their code files and maintain version tracking along with pull request management and collaboration by means of project comments.
Postman serves as a popular development API platform which allows developers to run tests while managing API documentation as well as inspecting their API endpoint performance capabilities.
The authorization process becomes faster through OAuth despite its security features. Users can trigger OAuth authentication through a single button interface which provides simpler authentication processes than multifaceted authentication methods.
The popular developer tools include Apigee for API management and APIMatic and API Transformer for SDK and code generation along with API Science for performance evaluation as well as serverless architectures for cloud-based API hosting and API-Platform as PHP framework with Auth0 for authentication and authorization and ClearBlade for IoT API management and GitHub for code management and collaboration and Postman for API testing and evaluation and Swagger as an open-source framework for API development.
API development delivers multiple strategic business advantages that include:
1. The system enables business innovation through the smooth implementation of new functional capabilities and service implementations.
2. Seamless independent delivery and upgrade capabilities of separate services constitute the main advantage of this method.
3. API development ensures both high system scalability and dependable operation performance for vital business services.
4. A secure posture emerges through the protection of sensitive information, together with defense against unauthorized system access.
5. Integration Costs decrease when the system integration duration is decreased and the implementation workload is reduced.